Why DDoS is More Dangerous for Cloud and Data Center Providers
Last week we continued our article series on DDoS protection in a connected world. This week we'll focus on how DDoS impacts the daily lives of data center professionals.
Here’s an important point many don’t realize. Distributed denial of service (DDoS) attacks are now an everyday occurrence. Whether a small non-profit or a huge multinational conglomerate, the organization’s online services — email, websites, anything that faces the internet — can be slowed or completely stopped by a DDoS attack.
Let’s pause here and explore why DDoS attacks are dangerous.
For the data center, colocation, hosting, and other service providers, DDoS attacks threaten the network and service availability infrastructure to all its tenants, subscribers, and customers and can target the most valuable customers.
A successful DDoS attack can seriously damage a brand’s reputation and cost hundreds of thousands or even millions of dollars in revenue. Moreover, DDoS attacks are sometimes used to distract cybersecurity operations while other criminal activity, such as data theft or network infiltration, is underway.
Another critical reason DDoS is more dangerous today than ever revolves around geopolitical tensions.
Recent events in Ukraine have demonstrated the efficacy of both state-sponsored and grassroots cybercriminals in launching politically-motivated DDoS attacks against critical infrastructure and government agencies.
Data Center Providers: Take this Warning Seriously
Just for a moment, let’s break down the fourth wall and have a conversation. As the author of this paper, I have a unique understanding of DDoS and cybersecurity threats and how they impact data centers. As an executive at a leading hyperscale and data center company, our ability to deliver consistently available connectivity and infrastructure services is paramount to success. However, one key trend I’ve noticed is that our customers are becoming even more dependent on connectivity and the underlying infrastructure supporting their business.
The threat of a DDoS attack has grown exponentially as reliance on critical infrastructure has grown. Believe me when I tell you that your data center and your critical infrastructure are always a target. The other significant trend I’ve seen is that DDoS attacks continue to grow in intensity, breadth, and complexity.
Suppose you have a DDoS solution, great job. You’re already ahead of the game. However, established solutions, which rely on ineffective, signature-based intrusion prevention or traffic rate-limiting, are no longer adequate. Please consider that entire statement. As a reflective point, when was the last time you reviewed your DDoS solution? Is it adequate?
Taking a step back, it’s key to also look at cloud providers. Remember, the dominant workload delivery model today is hybrid and multi-cloud. So, if your workloads are split between cloud and colocation, we need to discuss a few things. Cloud providers currently offer DDoS mitigation services directly to their tenants. However, while many tenants benefit from such services, others require additional DDoS protection options, particularly when they are targeted directly by complex attacks.
The reason for this is threefold:
- Cloud and data center providers’ DDoS mitigations aim to primarily protect their tenants against L3/L4 DDoS attacks, leaving them susceptible to L7 DDoS attacks.
- These L3/L4 countermeasures are generally deployed on a reactive, as-needed basis, which can delay the DDoS protection from kicking in by 1 – 2 minutes and are not inline.
- Cloud and data center providers generally offer a one-size-fits-all DDoS mitigation option that applies to every business vertical, lacking application-specific DDoS countermeasures.
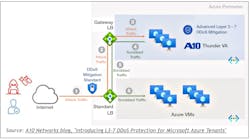
As a result, various businesses (e.g., gaming, finance, etc.) need additional customized DDoS mitigation solutions that provide more comprehensive and efficient coverage. For example, Microsoft Azure is closing this gap by allowing customers to add inline DDoS protection through network virtual appliances (NVAs) available in the Azure marketplace. This is made possible by using Azure’s Gateway Load Balancer (LB) feature. The Gateway LB ensures that relevant NVAs are injected into the ingress path of the internet traffic as it heads toward Azure-hosted applications and services.
We’re now thinking beyond the traditional security parameters and focusing on new and emerging threats. However, there is a significant challenge we have to overcome. How do you know if you have a legacy or modern solution protecting you from DDoS?
DDoS: Legacy vs. Modern Protection
By nature, DDoS attacks are largely brute force; they are often perceived as crude. Legacy DDoS defense solutions were designed to protect network infrastructure from attacks, leaving legitimate users without a connection to the online resources they need. Maintaining service availability for users during a DDoS attack is the primary reason to deploy a DDoS protection solution. The solution has failed if legitimate users can’t access the necessary tools. The focus should be on legitimate users and protecting network infrastructure.
Remember, effective DDoS defenses must be precise, with the ability to intelligently distinguish legitimate users from attacking bots. Solutions that focus on strategies like Remote Triggered Black Hole (RTBH) and service-rate limiting to detect attacking botnets fall short because they are indiscriminate and can block access for legitimate users. Meanwhile, legacy DDoS defense solutions rely primarily on bits per second (BPS) and packets per second (PPS) thresholds to protect infrastructure.
Here’s the big question, how do you know if your solution is still legacy? Consider this checklist:
- Your DDoS solutions rely on RTBH and traffic shaping
- You are prone to false positives and false negatives
- You have too many screens to analyze and suffer from the ‘swivel chair analysis’ problem
- You lack actionable threat intelligence
- The solution is ineffective against sophisticated targeted network and application layer attacks
- You still require extensive manual, reactive analysis, and intervention
That last point is key to understanding. We need to talk about automation and improved intelligence.
Not only does a DDoS attack diminish availability, but it also takes people away from valuable work.
No organization has unlimited people or resources. Because of that, efficiency is imperative. Yet legacy DDoS defense requires a lot of manual intervention during wartime. It also involves a lot of people to resolve network challenges and takes away from other critical business and technology priorities.
This is unsustainable for any organization. Not only does a DDoS attack diminish availability, but it also takes people away from valuable work. Instead of working on tasks that benefit the business, people are pulled into a firefight.
Organizations need automated DDoS protection strategies that eliminate the manual intervention often required to defend against attacks. Leveraging automation based on pre-set policies maximizes effectiveness while minimizing the chances of false positives, thus preserving resources by keeping them focused on essential tasks and not battling DDoS.
Another critical point is creating a defensive DDoS strategy in your primary locations and at the edge.
DDoS Defense at the Data Center and Cloud Edge
To overcome legacy DDoS protection challenges, look for solutions that scale to defend against the DDoS of Things and traditional zombie botnets. Further, your solutions must detect DDoS attacks through high-resolution packets or flow-record analysis from edge routers and switches. Unlike outdated DDoS defense products, modern DDoS defenses include detection capabilities across crucial network elements, including application delivery controllers, load-balancers, virtual network services, and more. These capabilities provide the context, packet-level granularity, and visibility needed to thwart today’s sophisticated attacks.
Download the entire special report, The Security Gap: DDoS Protection in a Connected World, featuring A10, to learn more. In our next article, we’ll shift our focus from experiencing these attacks to defending against them.